Let’s find out what it means to break the cipher.
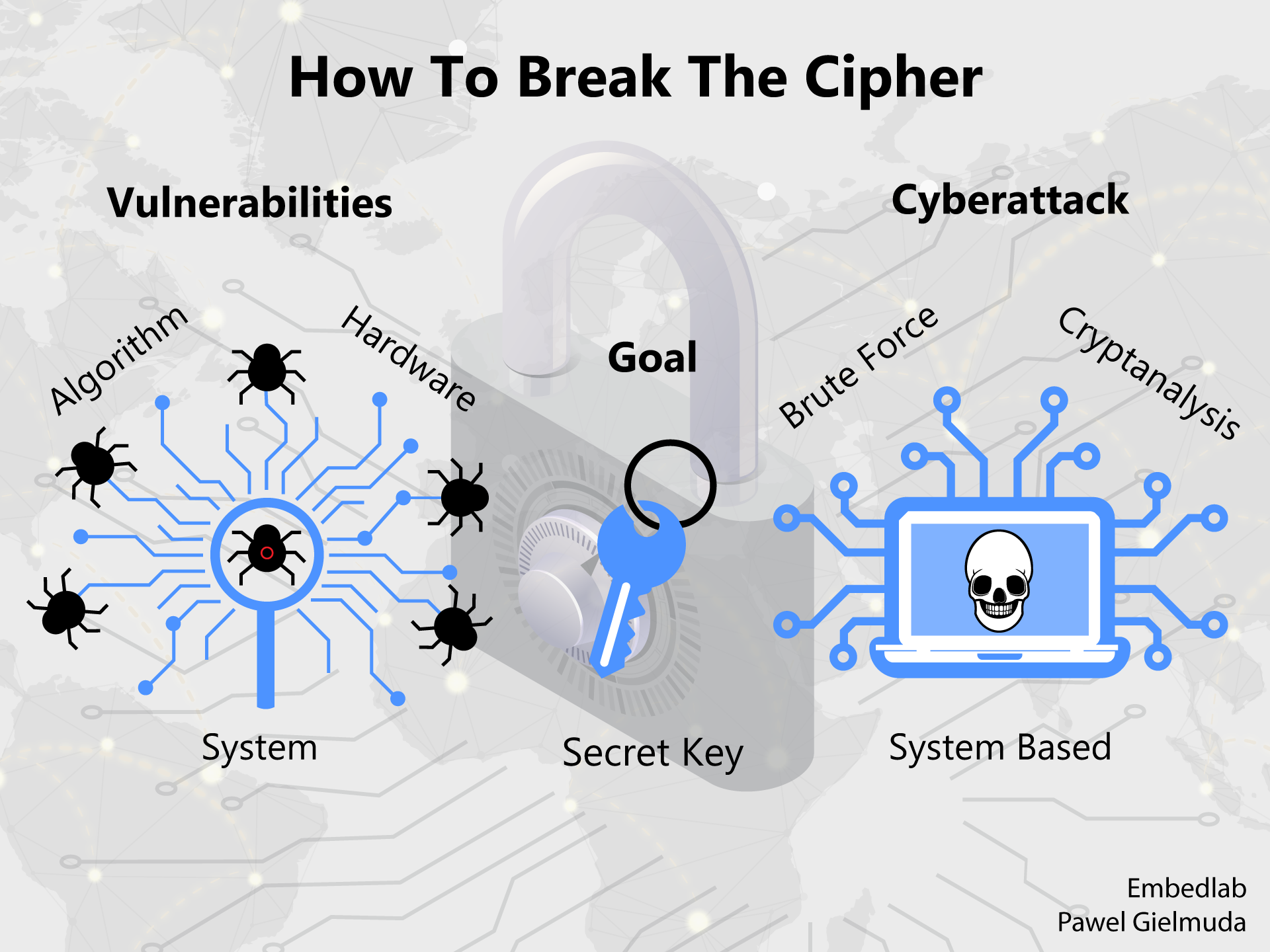
Someone may believe that the knowledge of how the cipher would be enough. However, in most cases, the algorithm is well known, but the goal is to find a secret key.
And how to do that? You can:
- check every possible value with a supercomputer -this is called a bruteforce attack,
- analyze ciphering process( i.e. compare plaintext vs ciphertext or the measure stolen hardware) to narrow key space and then check the most probable value — this is called cryptoanalysis,
- exploit some drawbacks of the ciphering system i.e. dependency between keys for following sessions which enable prediction of its value.
Finding out the key value in ideal cases (like for the One Time Pad algorithm) is impossible. But in real-world hackers can take advantage of some vulnerabilities which could be:
- algorithm related — in DES the algorithm assumed only a 56-bit key (7-character password) — this was not enough and could be found out by brute force attack
- hardware-related — measuring time or current consumption during a phase of encryption (i.e. XORing) could indicate when zeros and ones are in the key — it’s not simple but when it comes to money everything has its price,
- system-related — when next session secret key could be predicted with relatively high probability like in Netscape Navigator security issue.
There are much more things that need to be considered when implementing a unbreakable crypto system. However, the most important one is that when the key space is big and its value is as random as possible, the task for the hacker would be much more complicated.
Do you know any other idea to break the cipher? Share your views in comments.