We already know that symmetric ciphering is using one private key for the encryption and decryption process. It’s worth noticing that this option is used for the secure exchange of a large amount of data. Let’s discuss block ciphers.
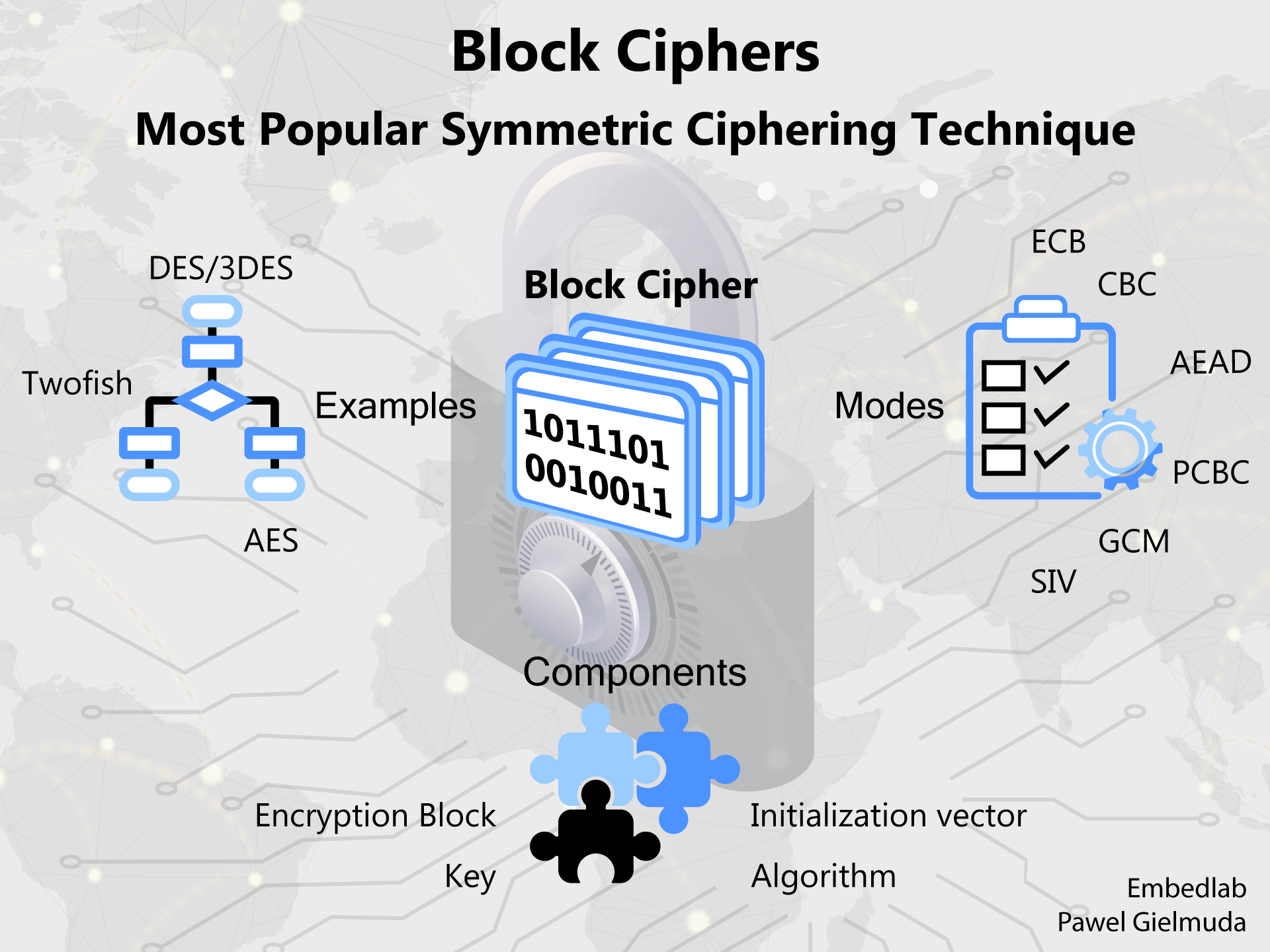
Symmetric methods could be further divided into stream and block ciphers and the last one is commonly used. The best example of that is AES which is the king of all ciphers. However, it’s worth noticing also its predecessor DES/3DES or niche competition Twofish.
How does it work? Block cipher always processes data in chunks i.e. 128 or 256 bits (encryption blocks). Every chunk is processed according to a publicly known algorithm. It i.e. permutates or swaps bits with predefined ones but details on how to do that depend on the secret key.
The output of the previous block processing combined with the next chunk of data is the input for the next turn. At the beginning of the data, a random initialization vector is added. Sometimes also padding is needed at the end so that the input data size will be a multiply of block size.
Initialization vector, padding, and the way the previous output block influences the next one are defined in the mode of operation. Modes could be faster (ECB mode), more secure (CBC mode), support parallel computing (CTR mode), or do not require padding (OFB mode) and lost of others.